Email is the lifeblood of many businesses — and its biggest security risk. That’s because scammers have become experts at gaining access to your business data with emails that trick people into taking actions that open the door. Your best defense? Educating your team on how to spot their tactics and not fall into the trap. This guide can help you do just that and improve your company’s email security.
Social Engineering
Remember the Trojan Horse? Not the virus, the wooden horse the Greeks used to enter the gates of Troy and win the Trojan War. That was social engineering.
Social engineering uses human psychology to exploit the weakest link in any security system — people. Scammers use deception to manipulate people into a variety of actions that provide them with confidential or personal information. They then use that information to gain access to more data and systems.
SIM swapping is a type of social engineering — where the scammer tricks a person at a mobile carrier that they are you and transfers your SIM card to another device. But, by far the most common and most successful (for the scammers) social engineering attack is phishing.
Phishing
Phishing got its name from the lure and hook approach of these social engineering emails. There are many different forms of phishing, but they all appear to be emails for reputable organizations. It’s common for scammers to piggyback on national events or news, such as:
-
- Health concerns (COVID-19 has been a boon for scammers)
- Weather alerts and or natural disasters
- Elections and other political events
- Holidays
- Charities or fundraising
- Security alerts or financial news
Phishing emails are designed to create a sense of urgency so users click before thinking or reading the email carefully. Common calls-to-action include:
- Update your account
- Your account has been suspended, login now
- Fraud has been detected, review your account
- You’ve received a message. Click here to read
- Donate now to save lives
- Confirm your $20 reward
- Update your payment details
- Download a file from {a familiar email address}
- And many, many more
Social engineering scammers are continually adapting their messages to catch people off guard and get the desired reaction. Emails sometimes have strange word phrasing, poor punctuation and misspellings — but scammers are getting more sophisticated all the time.
Scammers also make phishing emails believable by using your data they’ve already stolen. This is often called spear phishing. Emails may mention you by name, reference your company or phone number, or include other details that trick you into believing the email is from a real contact or organization with which you have a connection or account.
When spear phishing targets company executives it is called CEO fraud. Since CEOs often have complete access to company systems and accounts, CEO fraud is especially devastating for a company.
CEO accounts can also be spoofed to get reactions out of employees, a practice called whaling. After all, if you get an email that appears to be from your CEO telling you to pay a bill immediately, send a document to take some other actions, chances are you do it — fast.
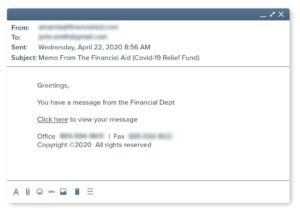
Examples Of Phishing Emails
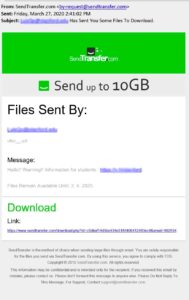
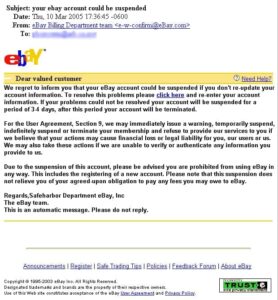
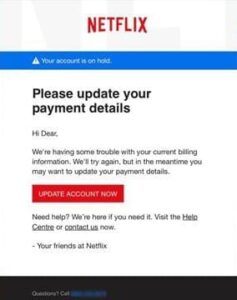
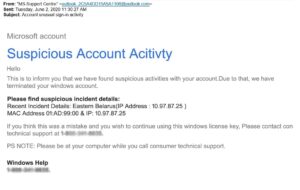
Here are actual phishing messages captured recently. Click on any image to see it larger.
Spotting A Phishing Email
Scammers are making it harder and harder to spot a phishing email. They use graphic design to mimic a trusted company both for the email and the landing pages that links are driven to. One of the easiest ways to spot a scam is to look at the URL.
In your email inbox, you can see where the links of emails are going without ever clicking on them. Simply put your mouse over the button or link and the destination url will appear at the bottom left of your screen. This image shows an example of an email signature. You can see that the link text (convergencenetworks.com) is in fact going to our url (https://convergencenetworks.com).
With phishing emails, the url doesn’t match the link text. Sometimes these urls are way off (e.g., futball.insystemcom.com). Other times they try to look close in some way but are not the same as if you went directly to the company’s website.
The from area of your email can also be spoofed. Not the from email itself, but the from name that is associated with it. Like with the URL, rolling over the from name can show you the actual address. Spoofing the from name is a common tactic in whaling — when spammers send out an email that appears to be from a company executive to spur action in other employees.
Spotting A Spoofed Site
Sometimes the URL alone is not enough to spot a spoofed site. Spammers can use tactics like pharming (sometimes called DNS poisoning) to redirect a genuine website url to a malicious website.
A red flag that this is happening is a change in the URL. Also the site is not likely to be secured, meaning the URL will start with http:// instead of https://. In many browsers secure sites have a small lock next to the URL to help users recognize it as secure.
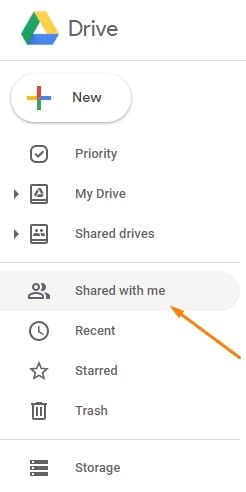
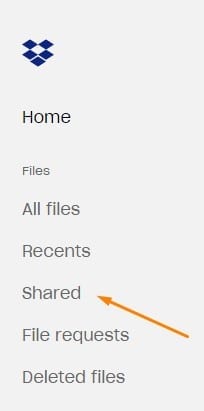
Another way that scammers fool you is by using a cloud service to host their malicious files. Called cloud phishing, this tactic uses emails containing links to forms or documents hosted on cloud services like Dropbox or Google Drive.
The best way to avoid this type of scam is to not click on links in emails for these services. Instead, keep a bookmark to your cloud services and access through there. Anything someone sent to you should appear under Shared in Dropbox or Shared with me in Google Drive. When in doubt, contact the sender to find out if they really sent you a file.
Your Best Defense Against Phishing Is Training
The one constant about phishing is how often it changes. Cyber criminals are becoming more sophisticated and adapt quickly to trends. That’s one reason why no firewall, mail filter or other security measures can block them completely. So your best defense is training your team about the dangers and how to avoid falling victim.
Here are some steps to help set up your training program:
- Have a complete IT Usage Policy that sets expectations and a baseline for protecting company data.
- Train your team on the policy. Don’t just hand it out, ask for a signature and move on — real prevention requires real training.
- Make cyber security discussions part of your regular employee meetings and communications. Add it to the agenda to remind about policies, but also share tips and real experiences that people are encountering.
- Report any suspected phishing attempt or breach to your IT and cyber security partners. They can not only help resolve issues in real time, but also help you adjust your cyber security over time to minimize your risk.
- Have a process that lets the rest of your company know about a phishing attempt. Scammers often target small groups of employees at once, and continue with the same attempt over and over until they get a bite. A simple warning can go a long way in making sure no one takes the bait.
- Simulate attacks to assess your staff response. This is a critical part of training. People learn much better with real world examples and simulations provide that with the added safety of not putting any data at risk.
Your Phishing Prevention Cheat Sheet
Here’s a quick list of dos and don’t to keep yourself from getting hooked by a phishing email:
-
- When in doubt, wait. Phishing works by making the user feel like they need to act NOW. Don’t. Any suspicious email should be reviewed carefully and shared with the IT security team before taking any action.
- Rollover the “FROM” name and any links or buttons. Make sure the URLs match the link texts and that they link to where you’d expect based on the “FROM” name and email address.
- Never enter your account or personal information on an http:// site. The “S” in https:// stands for security. Any genuine account login page or form will have an https:// url.
- Set up Multifactor Authentication and use an authentication app. Google Authenticator (App Store / Play) or Microsoft Authenticator (App Store / Play) are the most common. Avoid using SMS to authenticate when possible because it puts you at risk for SIM swapping.
- Don’t click to download files sent from cloud services, like Dropbox or Google Drive. First login to those services with saved links and looked in the shared folders. If the file isn’t there, contact the sender first to make sure it is a genuine email.
- Keep personal info off of public sites. Think about your most common security question answers, could scammers find them out by looking at your Facebook page? If they can, it’s time for a change. Taking the info off public sites will help, but you should also change your security answers to topics you’ve never posted about. Once online, data has a way of sticking around even after it’s deleted. Plus it might already have been captured in a previous breach.
- Keep your computers, phones and other devices up to date. Download and install system updates as soon as they are available. They often contain patches to known security holes.
- Avoid 3rd party email productivity apps. Apps like Edison, Cleanfox and Slice scrape data from your email to sell. While they specify that they “anonymize” the data, research has shown that stolen data can typically be tied back to specific people.
- Talk to the sender. Use a phone number or email you already have for the sender to verify that the email is real. Don’t click on any links, reply to the email or call the number provided in the email. If it is a real email asking for sensitive information, try to provide it directly over the phone. It’s never a good idea to send your social security numbers, account logins or credit card information in an email.
- Never download email attachments unless you are confident in the sender. And never download drivers or software patches. Your IT team should be maintaining this for you and can apply these remotely or over a secure connection.
- Use Microsoft Teams to cut down on your emails. The fewer you have to get through, the less likely you are to get hooked by a phishing attack.
- Keep in mind, emails aren’t the only mode of attack. The tactics in this guide can start with a phone call or text instead of an email. And many of these same prevention tips apply.