Why keep an eye on social engineering threat trends? Social engineering is the primary component of the overwhelming majority of cyberattacks today. Cyber thieves are leveraging these social engineering threat trends to directly perpetrate fraud, harvest credentials, or install malware.
Despite workers’ best efforts, cybercriminals continue to extort, defraud, and ransom companies for billions of dollars annually. As new defensive capabilities are created and put into place, crafty criminals look for new ways to defeat them.
While security-focused decision makers have prioritized strengthening defenses around physical and cloud-based infrastructure, human beings are quickly becoming the most reliable and easy entry point for compromise.
Sociability Leveraged as a Weakness
A wide array of content and techniques continue to be developed to exploit human behaviors and interests. The most effective methods prey on natural human tendencies and undermine instincts which raise an alarm that “something isn’t right.”
The intended victim is often presented with content they may already be familiar with or regularly interact with in their day-to-day jobs: receipts, documents, invoices, and spreadsheets.
The content appears routine and therefore raises no alarm. A threat actor might impersonate a trusted partner or an authority figure, such as a company’s executive.
Social interest is also frequently leveraged: at the beginning of the COVID-19 pandemic, there was a massive desire for information about updated health guidelines, company policies, regional mandates, and vaccine development.
Because of the universal relevance, threat actors of every sophistication level pivoted to make use of COVID-19 related content.
5 False Assumptions End Users Have About Cybercriminals
Since most office workers aren’t actively looking for phishing attempts or cybercriminal activity, it’s easy for them to make false assumptions about the nature of cyberattacks.
Here are five of the most common false assumptions:
- Cybercriminals will not spend time building rapport prior to executing attacks, like holding regular conversations
- Legitimate services, like those provided by authoritative technology companies like Google and Microsoft, are always safe to use
- Threats only involve their computer and not orthogonal technologies such as the telephone
- Threat actors don’t have access to email conversations held with colleagues and that those existing conversation threads are safe
- Threat actors won’t make use of timely, topical, or socially relevant content to exploit emotions or pique interest
Let’s dive into each of these false assumptions in more detail.
False Assumption #1: Criminals Won’t Hold Conversations with You
Effective social engineering is about generating feelings within an end user that mentally drives them into engaging with content. Something in their inbox is urgent and the other person seems trustworthy, so interacting with or helping the requester seems legitimate.
By sending innocent-appearing emails with the intent to lure the user into a false sense of security, cybercriminals lay the groundwork for a relationship to be more easily exploitable.
One particular type of threat is a Lure and Task Business Email Compromise (BEC) threat. These typically start with a benign conversation or ask a question to get the recipient to engage with the email.
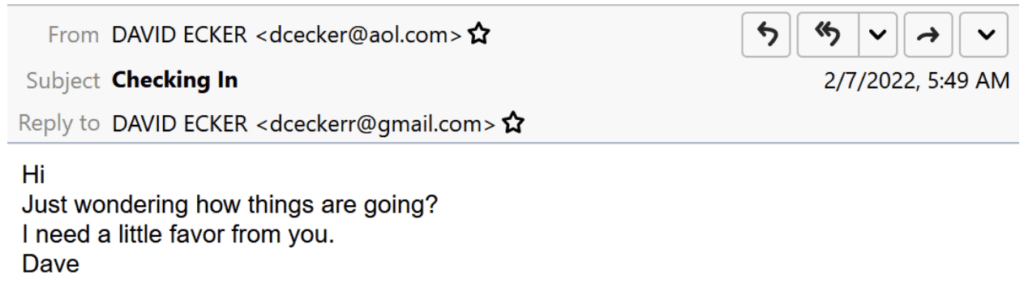
Lure/task emails are typically a gateway theme – if the victim replies, they may be led to another type of threat such as a gift card, payroll, or invoice fraud.
The cybercriminal then tries to get a recipient to engage with them and will send follow-up requests – such as transferring money – in future emails once a social connection has been established. The result can cost individuals and organizations thousands of dollars.
False Assumption #2: Google and Microsoft Services Are Always Safe
Coworkers may be more inclined to interact with content if it appears to come from a source they trust and recognize. However, threat actors regularly abuse legitimate services such as cloud storage providers and content distribution networks to host and distribute malware, as well as credential harvesting portals.
According to Proofpoint, Google-related URLs were the most frequently abused in 2021. However, when examining which domains are actually clicked, Microsoft-related URL-based threats earned more than twice the clicks of those hosted by Google.
This could help explain why analysis shows Microsoft OneDrive is the most frequently abused service by top-tier cybercriminals, followed by Google Drive, Dropbox, Discord, Firebase, and SendGrid.
False Assumption #3: Threat Actors Don’t Use the Phone
It’s not uncommon for people to think email-based threats exist only in computers. But in 2021, Proofpoint researchers found an increase in attacks perpetrated by threat actors leveraging an intricate ecosystem of call center-based email threats.
The threats require a lot of human interaction, something not regularly associated with phishing attempts. The emails themselves don’t contain malicious links or attachments, and individuals must proactively call a fake customer service number in the email to engage with the threat actor.
There are over 250,000 of these threat types each day.
There are two types of call center threat activity. One uses free, legitimate remote assistance software to steal money. The second leverages the use of malware disguised as a document to compromise a computer which can lead to additional malware.
The second attack type is frequently associated with BazaLoader malware and is often referred to as BazaCall.
Both attack types are considered telephone-oriented attack delivery (TOAD).
Here’s an example of a financially motivated TOAD threat pretending to be a PayPal invoice from a U.S. weapons manufacturer:
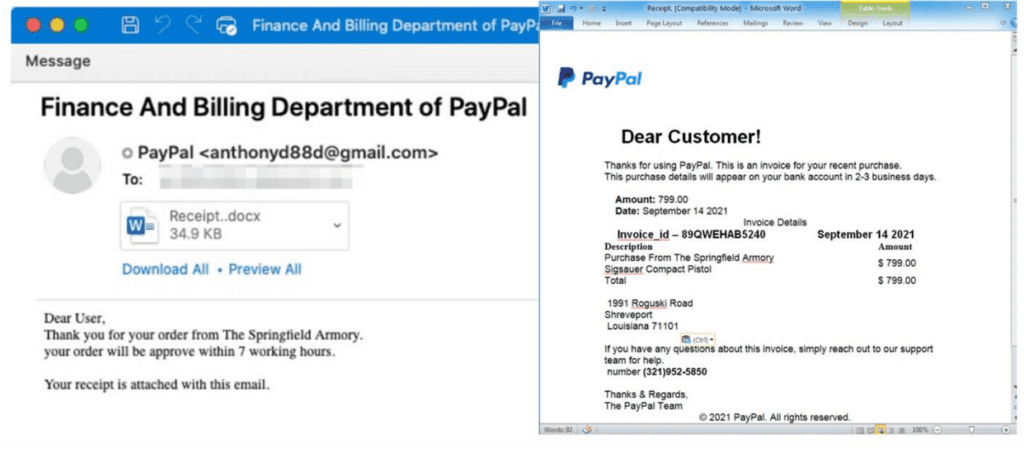
Victims can lose tens of thousands of dollars to these types of threats. In one case, Proofpoint identified a victim losing almost $50,000 to an attack from a threat actor masquerading as a Norton LifeLock representative.
False Assumption #4: Replies to Existing Emails are Safe
Thread hijacking, or conversation hijacking, is a technique where cybercriminals reply to existing email conversations with a malicious attachment, URL, or request to perform some action on the cybercriminal’s behalf. The criminal using this method exploits the person’s trust in the existing email conversation.
Typically, a recipient is expecting a reply from the sender and is therefore more inclined to interact with the affected content. To successfully hijack an existing conversation, cybercriminals need to obtain access to legitimate users’ inboxes.
There are multiple ways this can be achieved, including phishing, malware attacks, credential lists available on hacking forums, or password-spraying techniques. Threat actors can also hijack entire email servers or mailboxes and automatically send replies from threat actor-controlled botnets.
Email messages will appear legitimate, and because the threat is a reply to a recognized thread, the message history will be attached.
False Assumption #5: Cybercriminals Only Use Business-Related Content
Every year cybercriminals capitalize on current events, news, and popular culture. They use lure themes coinciding with things lots of people will be interested in to get people to engage with malicious content.
Researchers at Proofpoint observed a few BazaLoader campaigns leveraging Valentine’s Day themes such as flowers and lingerie in January 2021.
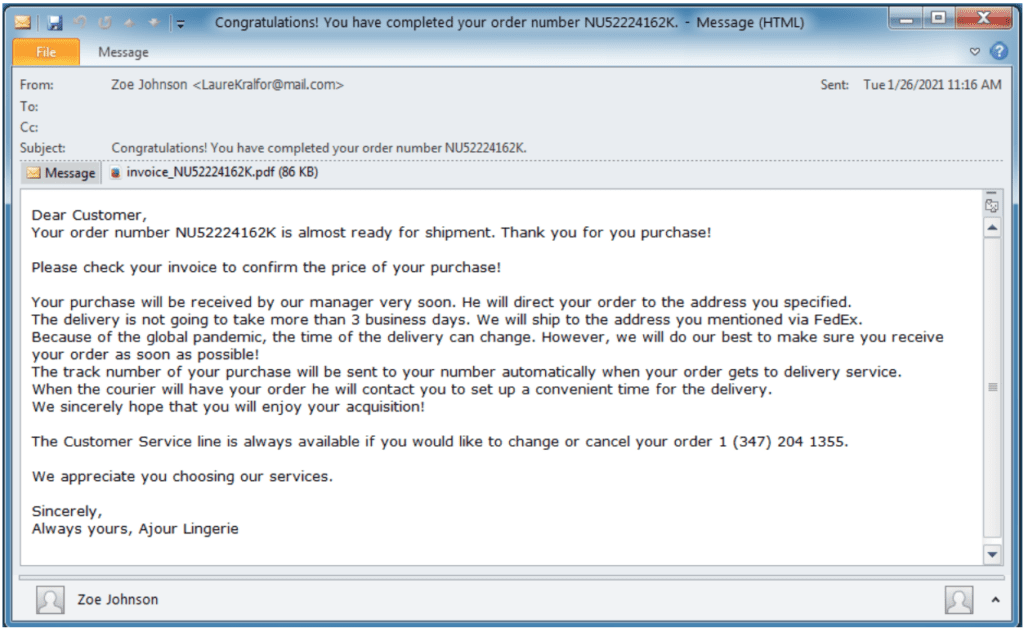
In 2021, BazaLoader cybercriminals began using infection chains that required a significant amount of human interaction, like visiting actor-controlled websites to download a payload, or even calling the threat actor directly to presumably get assistance with an erroneous purchase (as seen in the example image above).
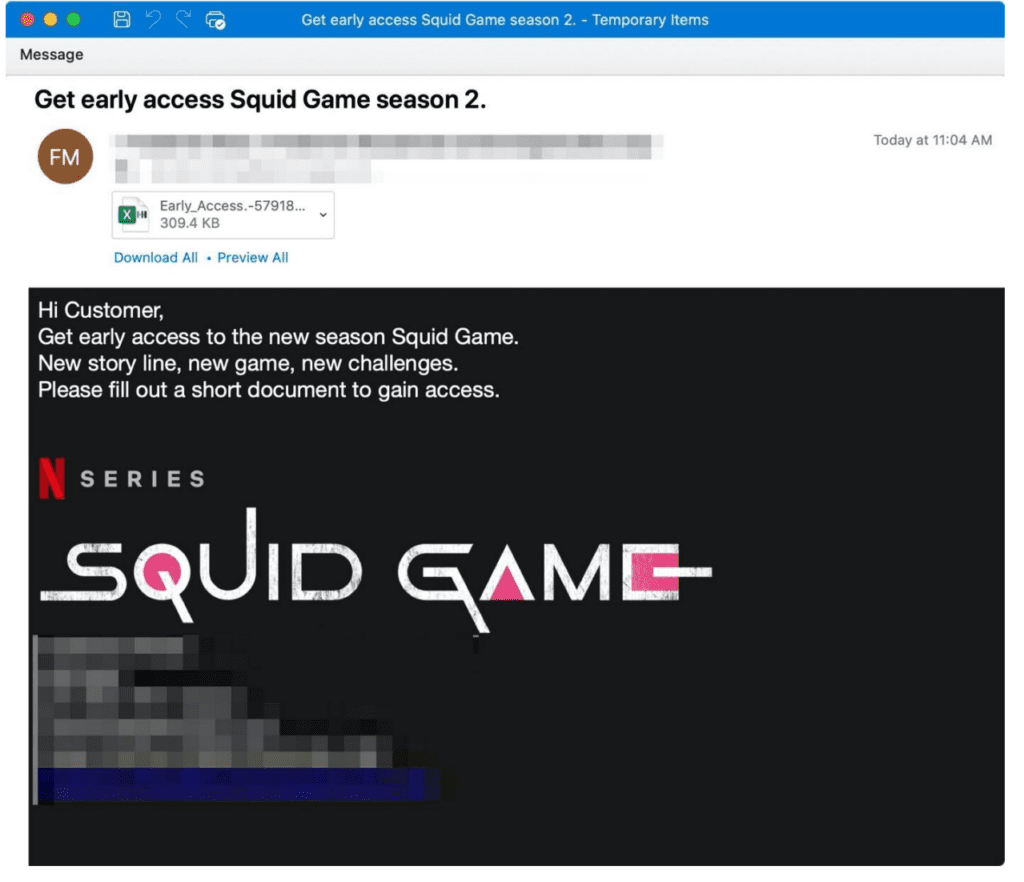
Another key example of cybercriminals using pop culture to target users happened in October 2021. Proofpoint identified the large cybercrime actor TA575 distributing the Dridex banking trojan using Squid Game themes.
The cybercriminal entity masqueraded as an organization associated with the Netflix global phenomenon. By using emails enticing targets to get early access to a new season of Squid Game or to become a part of the TV show casting, they persuaded end users to click on malicious links or downloads.
Key Insights for 2023
Now that you’ve read about the latest in social engineering threat trends, here are five key insights to take away:
- Threat actors may build trust with intended victims by holding extended conversations
- Threat actors expand abuse of effective tactics such as using trusted companies’ services
- Threat actors leverage orthogonal technologies, such as the telephone, in their attack chain
- Threat actors know of and make use of existing conversation threads between colleagues
- Threat actors regularly leverage topical, timely, and socially relevant themes
Next Steps
Cybercriminals are getting more and more creative as time goes on, willing to go the extra mile to gain access to your valuable information. Luckily, finding the right cybersecurity partner is easier than you think.
Contact us directly to discuss any cybersecurity issues you may have.
*The information and example images in this article were provided by Proofpoint, 2022.*














